Inherent security problems of QR codes
We developed Countermark to avoid the inherent security problems of QR codes. We understand sometimes you need to attach data to physical objects, electronic documents and signage.
The real sting in the tail with QRishing and QR fraud is that people are having to use their privately owned phones for two factor authentication on their work network.
These phones are hidden from corporate network administrators and may not be patched to the latest security level.
If these phones are connected to a corporate network, they represent a real threat to the host organisation.
Explanation, most companies will have a policy for blocking attachments to emails – PDF’s and JPG’s have been associated with email a long time and are unlikely to be blocked. These files can contain QR codes, the mail scanning software does not check for QR codes in the JPG or PDF.
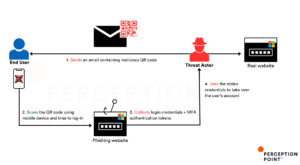
The email text will contain some credible reason or inducement for the email recipient to scan the malicious QR code.
Whereas some years ago private mobile phones would be banned from some parts of some organisations, the increasing use of phone-based authentication means that private phones, not necessarily patched are much more common in organisations and may be connected to an organisation’s internal network.
Or more bluntly, Microsoft Authenticator will run on Android 6 and up, only Android 11 -13 get security related updates. Staff with Android phones using Android 6 to Android 10 can use Microsoft Authenticator on phones with no current security patches.
An interesting post by Peleg Cabra, Senior Product Marketing Manager of Perception Point (see link below) backs up this theory:
“The emerging threat of QR code phishing or “quishing” demonstrates how threat actors always find new attack vectors to exploit human behaviours and evade detection.
In 2023 alone, #quishing attacks have surged dramatically targeting and successfully breaching organizations of all sizes worldwide. While quite simple to deliver, they easily bypass email security systems – most but not all (see 1st comment). #QRcode #phishing #detection #emailsecurity”
More information at www.Countermark.com
Perception Point article link:
Picture credit to Perception Point



